I normally don’t pay much attention to Windows apps, but since I knew calc.exe is just a dumb redirector that loads a Calculator app I eventually got curious and loaded the app into IDA. What caught my eye immediately was a number of exported functions:
- DllGetActivationFactory
- DllCanUnloadNow
- VSDesignerDllMain
When I queried my test win10 system for executables that contain these strings I discovered that pretty much all of them are Windows Apps. I then googled around trying to find out if there is any mention of these functions online, and in particular, how they are being used. I didn’t find anything interesting, but found some references, including this excerpt from an automatically generated build file:
#if (defined(_M_IX86) || defined(_M_AMD64)) && !defined(_VSDESIGNER_DONT_LOAD_AS_DLL) #if defined(_M_IX86) #pragma comment(linker, "/EXPORT:DllGetActivationFactory=_DllGetActivationFactory@8,PRIVATE") #pragma comment(linker, "/EXPORT:DllCanUnloadNow=_DllCanUnloadNow@0,PRIVATE") #pragma comment(linker, "/EXPORT:VSDesignerDllMain=_VSDesignerDllMain@12,PRIVATE") #pragma comment(linker, "/INCLUDE:___refMTAThread") #elif defined(_M_AMD64) #pragma comment(linker, "/EXPORT:DllGetActivationFactory=DllGetActivationFactory,PRIVATE") #pragma comment(linker, "/EXPORT:DllCanUnloadNow,PRIVATE") #pragma comment(linker, "/EXPORT:VSDesignerDllMain,PRIVATE") #pragma comment(linker, "/INCLUDE:__refMTAThread") #endif
So, looks like the building script depends on the _VSDESIGNER_DONT_LOAD_AS_DLL variable. I installed the latest Visual Studio trial version and queried all files for the ‘VSDesignerDllMain’ and ‘_VSDESIGNER_DONT_LOAD_AS_DLL’ strings… and didn’t get many results either…
Just a few files:
- Microsoft.VisualStudio.DesignTools.Utility.dll
- Microsoft.VisualStudio.TestPlatform.BuildTasks.dll
- Microsoft.Windows.UI.Xaml.81.Build.Tasks.dll
- Microsoft.Windows.UI.Xaml.Build.Tasks.dll
Their code didn’t really explain much (none of them actually refer to code using the ‘VSDesignerDllMain’ function, only generate files containing references to it).
So, I am curious what is the purpose of these functions… either some legacy tool, or some internal testing platform? ‘VSDesigner’ suggests IDE integration of some sort – potentially quicker way to debug the app? Anyway, just guessing here… If you are a Windows App programmer, or spent more time on reversing Apps and know how these are being used I’d be grateful if you could share.
In terms of code, the function simply calls the _DllMainCRTStartup function after setting the internal variable VSDesignerDllMain_status to 3, the DllMainCRTStartup eventually calls DllMain function:
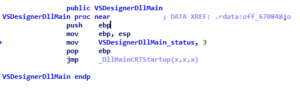 So, we have 2 entry points – one for the Windows exe (‘start’) and the second one for the DLL (‘VSDesignerDllMain’->’DllMain’)
So, we have 2 entry points – one for the Windows exe (‘start’) and the second one for the DLL (‘VSDesignerDllMain’->’DllMain’)
In the mean time, a typical Windows App is like a Frankenstein’s monster – it is a MZ DOS executable, a PE executable & DLL in one, a .NET assembly, a HTML/XAML madness, and… it can’t be even launched directly from the Explorer, because it needs to be activated via one of the 3 methods offered by the IApplicationActivationManager COM interface (AFAIK, not sure if there is any other way). While the plot thickens the platform gets more and more complicated and reversing work harder and harder…





