This part is more about archaeology than anything else.
The built-in SHIM database includes a number of test shims, which I will cover below.
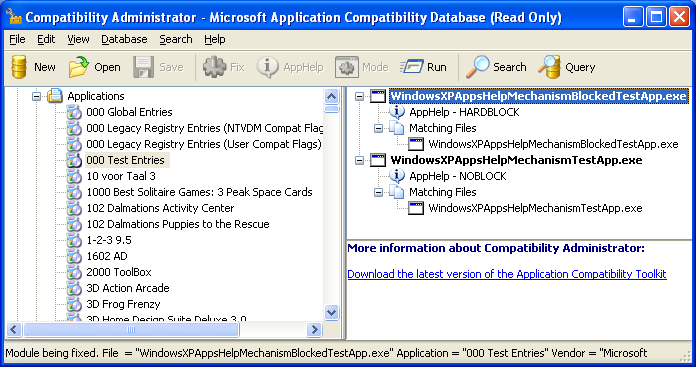
On Windows XP, you will find these two:
So, if you happen to name your executable one of these:
- WindowsXPAppsHelpMechanismBlockedTestApp.exe
- WindowsXPAppsHelpMechanismTestApp.exe
you can immediately see their effect after you try to run them on XP:
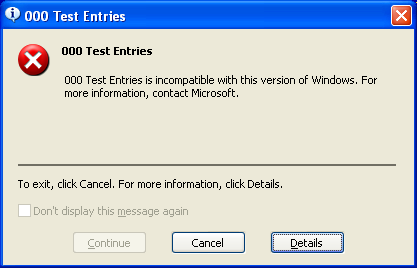
WindowsXPAppsHelpMechanismBlockedTestApp.exe
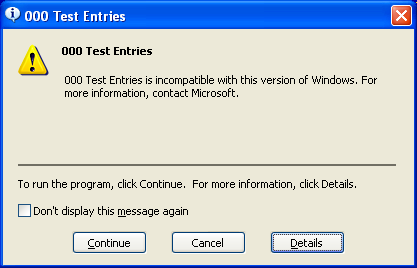
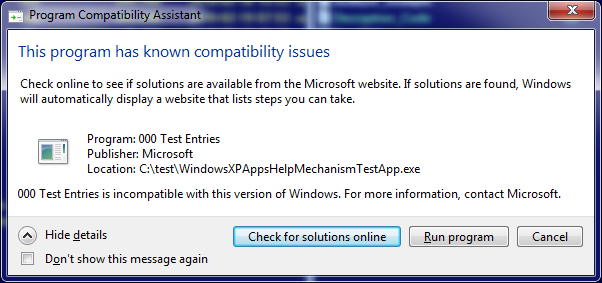
WindowsXPAppsHelpMechanismTestApp.exe
On Win7 we got a few more:
- AppsHelpMechanismTestAppBadMsg.exe
- AppsHelpMechanismTestAppBadMsgBlocked.exe
- WindowsXPAppsHelpMechanismBlockedTestApp.exe
- WindowsXPAppsHelpMechanismTestApp.exe
The first one runs with no issues.
The second one is blocked without any indication.
The visible messages are as follows:
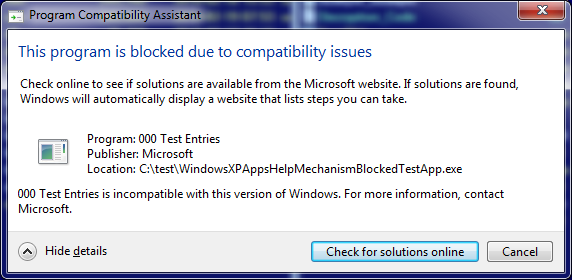
WindowsXPAppsHelpMechanismBlockedTestApp.exe
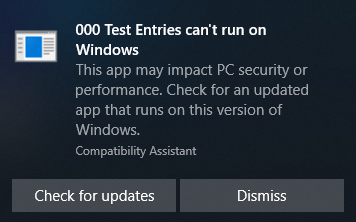
WindowsXPAppsHelpMechanismTestApp.exe
Finally, on Win10 it goes as follows:
- AppsHelpMechanismTestAppBadMsg.exe
- AppsHelpMechanismTestAppBadMsgBlocked.exe
- BlockedTestApp_AMD64.exe
- BlockedTestApp_AMD64_ANY.exe
- BlockedTestApp_WOW64.exe
- BlockedTestApp_X86_AMD64.exe
- BlockedTestApp_X86_ANY.exe
- BlockedTestApp_X86_WOW.exe
- WindowsXPAppsHelpMechanismBlockedTestApp.exe
- WindowsXPAppsHelpMechanismBlockedTestApp2.exe
- WindowsXPAppsHelpMechanismBlockedTestAppSpecific.exe
and visible outputs are:
AppsHelpMechanismTestAppBadMsgBlocked.exe /
BlockedTestApp_WOW64.exe /
BlockedTestApp_X86_AMD64.exe /
BlockedTestApp_X86_ANY.exe /
BlockedTestApp_X86_WOW.exe /
WindowsXPAppsHelpMechanismBlockedTestApp.exe /
WindowsXPAppsHelpMechanismBlockedTestApp2.exe /
WindowsXPAppsHelpMechanismBlockedTestAppSpecific.exe
Okay. That’s it.
Hmm not really… digging through internals of SDB on Windows 10 one more time I gathered the following (and hopefully complete) list of all the the test suite items:
- AppsHelpMechanismTestAppBadMsg.exe
- AppsHelpMechanismTestAppBadMsgBlocked.exe
- BlockedTestApp_AMD64.exe
- BlockedTestApp_AMD64_ANY.exe
- BlockedTestApp_WOW64.exe
- BlockedTestApp_X86_AMD64.exe
- BlockedTestApp_X86_ANY.exe
- BlockedTestApp_X86_WOW.exe
- WICAMockAppReinstallUpgrade.exe
- WICAMockAppReinstallUpgrade2.exe
- WICAMockAppReinstallUpgrade3.exe
- WICAMockAppReinstallUpgradeInfo.exe
- WICAMockAppReinstallUpgradeWarn.exe
- WICAMockAppReinstallUpgradeWarnBackup.exe
- WindowsTH_BlockedSetupTestApp.exe
- WindowsTH_TestApp_HardBlock_FWLink.exe
- WindowsTH_TestApp_HardBlock_KBArticle.exe
- WindowsTH_TestApp_HardBlock_NoInfo.exe
- WindowsTH_TestApp_HardBlock_StoreId.exe
- WindowsTH_TestApp_HardBlock_Wildcard1.exe
- WindowsTH_TestApp_HardBlock_Wildcard2.exe
- WindowsTH_TestApp_SoftBlock_FWLink.exe
- WindowsTH_TestApp_SoftBlock_KBArticle.exe
- WindowsTH_TestApp_SoftBlock_NoInfo.exe
- WindowsTH_TestApp_SoftBlock_StoreId.exe
- WindowsXPAppsHelpMechanismBlockedTestApp.exe
- WindowsXPAppsHelpMechanismBlockedTestApp2.exe
- WindowsXPAppsHelpMechanismBlockedTestAppSpecific.exe
- WindowsXPAppsHelpMechanismTestApp.exe
- WindowsXPAppsHelpMechanismTestApp2.exe
- WindowsXPAppsHelpMechanismTestAppSpecific.exe
So, how could you use it for malicious purposes? I dunno… One thought I have is about emulators. If you created a child process using one of these names (creation of such process should fail by SHIM design), could you use the successful exitcode from that process to detect an emulator?