This Registry entry:
HKLM\Software\Microsoft\Windows\CurrentVersion\Group Policy\Test\AdmParseLibrary=<DLL>
is of interest as it relates to TestHooks library that is loaded when *.admx template files are being parsed.
This Registry entry:
HKLM\Software\Microsoft\Windows\CurrentVersion\Group Policy\Test\AdmParseLibrary=<DLL>
is of interest as it relates to TestHooks library that is loaded when *.admx template files are being parsed.
A few days ago, I have received the following note from mike.zhang@domainregistrar [.] net [.] cn:
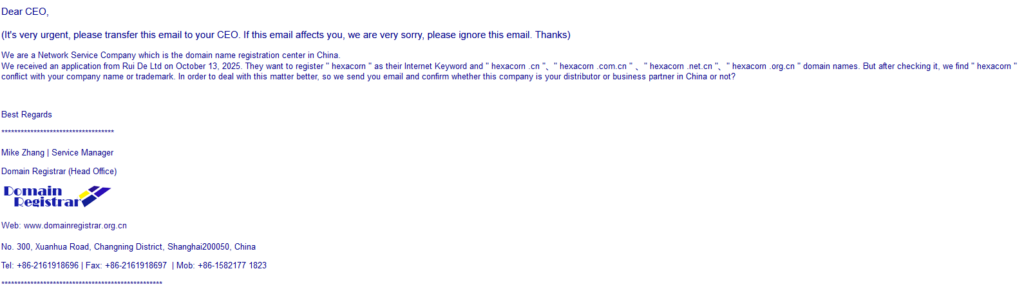
Without thinking too much, I replied that I don’t know that company.
Darn, that was the hook.
Scammer – Adam: 1:0.
A few days later, a dude from zhou_jianhua@263 [.] net sent me this emotionally charged message:
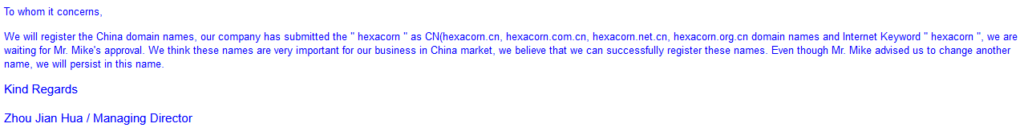
Now, this obviously triggered my interest, for many reasons.
While the first email acted as a hook and was kinda casual and ‘business as usual’, at least when it comes to domain ownership, this new one was meant to elevate my anxiety and trigger me to respond.
Luckily, I am quite sensitive to emails that trigger me emotionally.
First of all, the name of this web site is unusual, because it is a portmanteau of two words ‘hexadecimal’ and ‘unicorn’. For anyone to claim this name is in any way important to the Chinese market is laughable, to say the least.
Additionally, the meaning of ‘hex acorn’ in English is this:
A hex acorn nut is a hexagonal nut with a domed, capped top that encloses the end of a screw or bolt.
Yup. Literally, this:

So, I replied to the dude pretending that I care and am now waiting for a reply.
Will he read this post? I doubt.
So, hopefully there will be part 2 with an update.