While ADS is not widely supported/used by many apps (maybe with a notable exception of malware :)), it can be still used for some interesting purposes. In this short article, I describe a few legitimate uses of ADS by Windows programs that I know of.
If you know some others or if you spot any mistake, please let me know. Thanks.
This post is loosely based on this Microsoft list, but it contains some more details and looks at these streams from a ‘forensic angle’.
:$DATA
Standard ADS representing a content of the file.
:$WIMMOUNTDATA
This one is referenced by wimgapi.dll, wimserv.exe and recimg.exe (win8), but I don’t have more information about it.
:TASKICON_%d
This one is referenced by ieframe.dll (win8).
:Zone.Identifier
This is a name of a stream generated by Microsoft applications when user saves files to the local file system from a different security zone (e.g. Internet -> Disk).
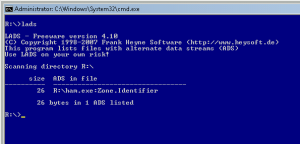
The content of the file is just an information about the original Zone the file comes from:

Good news: presence of the stream confirms (in a ‘most likely’ CYA fashion) the file has been downloaded from the internet.
Bad news: Interestingly enough, some malware samples attempt to delete the :Zone.Identifier ADS attached to their executables immediately after they are executed – I guess it’s because they want to:
- remove the ‘flag’ from the file that highlights it as ‘downloaded from internet’ – yet another subtle anti-forensics in action
- ensure that next time the file is launched (either via autostart entry or manually), it doesn’t pop up the ‘Are you surely sure you want to run this highly insecure program downloaded from the internetz’ message box
The code responsible for creating the :Zone.Identifier ADS is present in multiple system DLLs because the functionality is provided via IZoneIdentifier interface. The actual code adding stream is present in shell32.dll. (note: this and other code references is my best guess based on a quick grepping exercise on strings exported from all OS DLLs within system32 directory)
:favicon
This is a less known ADS that is being used by Internet Explorer. It acts as a cache and stores the favicon of the web site that has been bookmarked by the user.
It can be stored in files Page.url:favicon:$DATA; newer versions of IE appear to be also using format Page.website:favicon:$DATA
The content is just an .ico file – it can be extracted from a live system using ‘more’ command:

Previewing the extracted icon in Irfanview (and resizing it since it’s 16×16 pixels) shows the following picture (in my example BMI bookmark):
 as shown in the properties window:
as shown in the properties window:

The good news: from a forensic perspective it could be an interesting information to provide in a final report if the user activities are discussed. Presence of this ADS indicates that the site the favicon refers to has been added most likely manually by the user (of course, ‘most likely’ in a CYA fashion since we can’t exclude 100% the possibility of malware adding it).
The bad news: if you want to experiment with this feature, I must warn you that various versions of IE are buggy when it comes to preserving the favicons. So, they may not be present on all versions of IE. I have not done an extensive study as I don’t have various versions of IE at hand, but quick & dirty experiments show that bookmarks I added under IE8 preserve :favicon stream, the IE9 doesn’t. Again, this is best to be tested for the particular version of IE.
Again, good news is that if you find it on the analyzed system, you may get some clues from it. And if you don’t find it, well – one less artifacts to look at 😉
If you want to play around, use procmon and use filter Path Contains ‘favicon‘
Code responsible for :favicon ADS can be found in ieframe.dll
:OECustomProperty
This is a stream created by Microsoft Outlook Express/Windows Mail. I don’t have an example at hand.
The code is stored in inetcomm.dll.
:Encryptable
Attached to Thumbs.db files and created when pictures are viewed in Thumbnail mode.

The same directory enumerated for ADS before thumbnail and after turning into Thumbnail mode

The code is stored in thumbcache.dll.
Document Properties Stream Name
This is a ‘garbage’ ADS one can see immediately after playing around with properties of a file stored inside a folder. The most known ADS is probably ‘{4c8cc155-6c1e-11d1-8e41-00c04fb9386d}‘ (you can often see it in Procmon output).
Creating these is easy – one needs to e.g. change the title in the file properties box:

The same directory enumerated for ADS before the and after changing the title:

AFP_AfpInfo and AFP_Resource
Macintosh streams as explained on Microsoft web site. I don’t have more info about this one.
{59828bbb-3f72-4c1b-a420-b51ad66eb5d3}.XPRESS
XPRESS Stream is used during remote differential compression as explained on Microsoft web site. XPRESS is a compression algorithm and streams appear to be using when the compressed data is being downloaded. I don’t have more info about this one and at the moment I don’t know how to create a demo (show its creation on the system). Googling around, one can come across similarly named streams e.g.
- {59828bbb-3f72-4c1b-a420-b51ad66eb5d3}.rdc.1
- {59828bbb-3f72-4c1b-a420-b51ad66eb5d3}.rdc.2





