Detecting malware on a live system is often very difficult and requires special tools and lots of experience.There are situations though when some simple techniques can be used as well. This post introduces one such technique and provides a simple demo tool (toy really) you can use to play around.
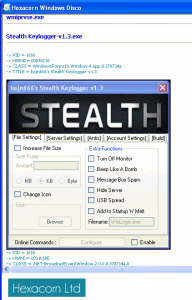
The technique itself relies on a simple fact that many keylogging malware apps utilize a hidden ‘worker’ window and often offer extensive GUI that is not typically visible, but can be accessed by a malicious user after pressing a combination of keys. Worker window receives all intercepted keystrokes that are being sent by a hook procedure and GUI is used to set up keylogger parameters/view logs, etc. So, since such ‘working’/hidden GUI windows are not visible to the user, but they are still windows one can still enumerate them and present them to the user (even if windows are invisible).
This is exactly what Windows Disco does. It walks through all processes and their windows and takes a screenshot of each window, then saves it to a temporary PNG file in a current subfolder (named disco); you may review all these files either in an application itself, or in an Explorer, IrfanView or other image viewer.
For naysayers: yes, of course this can be so easily bypassed and is of course not foolproof – everything can be hooked and both enumeration and screenshot-taking prevented as well as keylogging can be implemented in a different way, but this is a demo of a trivial technique, not a ‘solve it all’ software 😉 who knows… with more and more malware moving back from kernel to userland such simple techniques may turn to be actually useful.
Another similar technique that might be potentially useful is hotkey enumeration – provided that keylogger registers a hotkey in a documented way one could use a hotkey enumeration tool to find suspicious associations (again I know this is far fetched, many keyloggers use state machine to trigger their hidden GUI, but always… ). The tool + src to enumerate hotkeys and article in Russian can be found here and here.
As usual, testing on VM first is advised. Occasionally the GUI may be less responsive, pls be patient and kill it if necessary.
The whole procedure ends when MessageBox pops up showing how many windows have been enumerated.
The following screenshots have been taken from various keylogging applications; as you can see some are more ‘ostentatious’, some less.
As mentioned earlier, all files are saved in a ‘disco’ directory and can be reviewed using various browsers:

You can download HWD here.