The 2nd part following my first take on this subject was kinda inevitable.
Why?
Sixtyvividtails is one of my fav researchers, because a) he reads my posts, breaks them apart, and usually comes up with some amazing/creative comments/additional thoughts that often lead us to some new, cool discoveries (see f.ex. this) b) he also made a social media bet that I (obviously) couldn’t leave unchallenged. Thank you Sixtyvividtails, you are an inspiration and I love your research and creative ideas a lot!
So, to business…
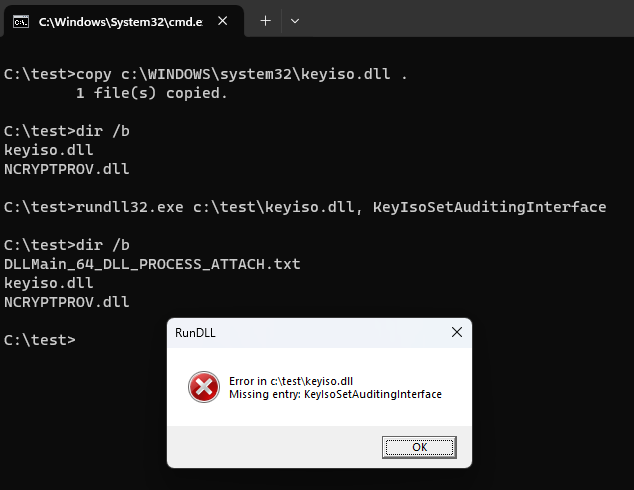
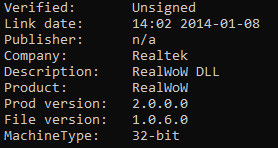
My first find was this unsigned Realtek DLL (RealWoWDLL.dll – VT Link) that exported the intriguing forward:
testker -> kerberos.Spinitialize
Then… I went for holidays 🙂
I did go there with an idea though that after coming back I will do a more structured follow-up research…
So when I came back, I immediately got to work.
The first target was an obvious one – run the very same forwarder-extractor script over the Windows 2025 server files. The results are here. Many of these combos can be used for DLL ForwardSideloading.
The second target was bigger. I checked my repo of ‘good’ files only to discover that I am sitting on around 700K ‘clean’ DLLs, both 32- and 64-bit. Sadly, I don know which ones of them are truly signed or not, unless the actual PE file of the DLL is physically signed (aka not via a catalogue). Still, 700K files is a lot, and there is a hope that it’s worth analyzing them all to see how many of them are non-Microsoft, and actually use/leverage the forwarded exports…
So, I ran my script over the last weekend and after few days it spat out its results.
And here’s the catch:
- yes, some vendors do appear to be using forwarded functions same as Microsoft and Realtek
- many functions that have their names exported by DLLs (mapping present in the export table) are not necessarily meant to be used by any other program, but since some do include a “.” character in their name, they could actually be used to facilitate DLL ForwardSideloading !
See the (filtered) results here.