Wine is a free implementation of Windows on Unix. That’s what the Wine web site says. To a malware analyst though, Wine is a free analysis platform that can be leveraged to analyze Windows executables.
How so?
It’s all thanks to the various so-called debug channels that Wine offers. Some of these channels – when enabled – turn Wine into a fully-blown tracer, an API monitor, or a complete log madness that includes any possible messages from Wine.
I won’t cover here how to install Wine, but you should easily find a recipe online. Once installed, it’s ready for a few quick tests that will demonstrate its main monitoring features (from the malware analysts’ perspective):
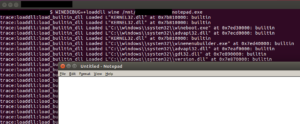
- Showing a list of loaded/unloaded modules (during run-time)
- Showing list of API calls and their return values
- Absolute tracing madness (yet still meaningful)
A number of channels can be combined, f.ex. one can run the following command:
-
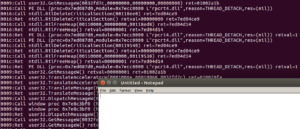
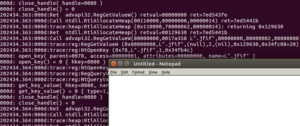
WINEDEBUG=+relay,+tid,+timestamp
to prepend the API log with a timestamp, and the TID (thread ID) of the current thread executing the API inside the process:
202729.726:0024:Call ntdll.RtlAllocateHeap(00110000,00000000,00000020) ret=7ed13224 202729.726:0024:Ret ntdll.RtlAllocateHeap() retval=00118ac8 ret=7ed13224 202729.726:0024:Ret rpcrt4.I_RpcGetBuffer() retval=00000000 ret=7ed57c45 202729.726:0024:Call rpcrt4.NdrServerContextNewMarshall(00b4e718,00119078,7ed55770,7ed612a4) ret=7ed57c81 202729.726:0024:Call ntdll.RtlFreeHeap(00110000,00000000,00118fc0) ret=7ed14071 202729.726:0024:Ret ntdll.RtlFreeHeap() retval=00000001 ret=7ed14071 202729.726:0024:Call ntdll.RtlReleaseResource(0011909c) ret=7ecfc83c 202729.726:0024:Ret ntdll.RtlReleaseResource() retval=00000000 ret=7ecfc83c 202729.726:0024:Call ntdll.RtlDeleteResource(0011909c) ret=7ecfb4a7 202729.726:0024:Ret ntdll.RtlDeleteResource() retval=00000000 ret=7ecfb4a7 202729.726:0024:Call ntdll.RtlFreeHeap(00110000,00000000,00119078) ret=7ecfb4bb 202729.726:0024:Ret ntdll.RtlFreeHeap() retval=00000001 ret=7ecfb4bb 202729.726:0024:Ret rpcrt4.NdrServerContextNewMarshall() retval=001166a8 ret=7ed57c81 202729.726:0024:Call ntdll.RtlAllocateHeap(00110000,00000008,00000018) ret=7ed03c9c 202729.726:0024:Ret ntdll.RtlAllocateHeap() retval=00118c20 ret=7ed03c9c 202729.726:0024:Call ntdll.RtlAllocateHeap(00110000,00000008,00000030) ret=7ed04c44 202729.731:0024:Ret ntdll.RtlAllocateHeap() retval=00118fc0 ret=7ed04c44 202729.731:0024:Call KERNEL32.WriteFile(00000024,00118fc0,00000030,00b4e748,00000000) ret=7ed0cc8f 202729.731:0018:Ret KERNEL32.ReadFile() retval=00000001 ret=7ec72d02 202729.731:0018:Call ntdll.RtlAllocateHeap(00110000,00000000,00000018) ret=7ec6be06 202729.731:0018:Ret ntdll.RtlAllocateHeap() retval=0011b888 ret=7ec6be06
A few notes at the end:
- Wine supports both 64- and 32- Portable Executables
- There are 400+ different channels; I will lie if I say that I know what all of them trace
- Obviously, running executables under Wine is a subject to various sandbox detections, including these I described in the past.
- The analysis could be automated to produce a decent sandbox report; while it can’t compete with commercial sandboxes, it may be a a decent solution for in-house analysis, especially for small companies (and as an alternative, complementary sandbox)
- If combined with other free solutions, may provide a secondary sandbox for differential analysis i.e. certain artifacts could be compared between 2 sessions (f.ex. one in cuckoo and one in Wine) and help in highlighting ‘randomness’ of some artifacts f.ex. mutex names, files created, etc.
- Since it is running natively on Linux, lots of tools are available out of the box that may help in scripting and data processing
- The source code is available and you can modify it to your purposes (f.ex. add automatic yara rule generation for specific artifacts, automatic URL extraction, etc.)
- Last, but not least – it won’t work with some executables – it still has bugs & features that are not implemented yet
All in all, yet another tool that may sometimes come handy.