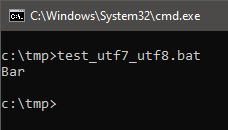
What will the following bat file print? Foo, or Bar?
@echo off
mode con cp select=65000 > nul
set jump=+ACQ-
mode con cp select=437 > nul
goto %jump%
:+ACQ-
echo Foo
goto :eof
:$
echo Bar
goto :eofHere’s the answer:
Batch files can be saved as text files using different encodings, including UTF7, and UTF8 as well as MBCS/DBCS characters sets.
One can therefore enforce encoding and change it not only outside of a batch file, but also on the fly, as is the case in the example above. As a result, the part of the code that executes after first ‘mode’ is encoded in UTF7 (‘+ACQ-‘ is an encoded ‘$’ sign), and the second is OEM-US English.
The below example replaces UTF7 in the above example with Traditional Chinese:
@echo off
mode con cp select=950 > nul
set jump=§A¦n
mode con cp select=65001 > nul
goto %jump%
:§A¦n
echo Foo
goto :eof
:ä½ å¥½
echo Bar
goto :eofIf you look at this code using 950 character set (big5) you will see this:
@echo off
mode con cp select=950 > nul
set jump=你好
mode con cp select=65001 > nul
goto %jump%
:你好
echo Foo
goto :eof
:雿末
echo Bar
goto :eofand if you choose to preview as UTF8:
@echo off
mode con cp select=950 > nul
set jump=§A¦n
mode con cp select=65001 > nul
goto %jump%
:§A¦n
echo Foo
goto :eof
:你好
echo Bar
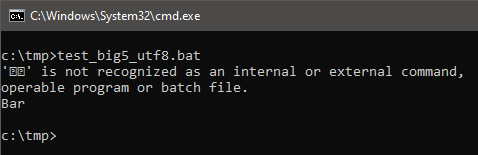
goto :eofMisleading, isn’t it?
When you run this version of script you will see an error from the interpreter – this is a result of it interpreting superfluous UTF8 prefixes that seem to be appearing out of nowhere within the interpreter. Perhaps further study of cmd.exe internals can help to eliminate this quirk. Still, the jump goes to the proper label & errors can be always hidden with standard error redirection: