LastSystemRITEventTickCount is a member of a _KUSER_SHARED_DATA structure. If you google for this particular field’s description you will eventually find sth along these lines:
Time in tick count for system-wide last user input across all terminal sessions. For MP performance, it is not updated all the time (e.g. once a minute per session). It is used for idle detection.
Since the user input is quite important from the sandbox perspective detecting changes (or lack of) of this particular field can act as a trivial (a.k.a. lame) anti-sandboxing trick.
Consider a simple routine like this:
mov edx,ds:[7FFE02E4h] ; get LastSystemRITEventTickCount back: pushad invoke Sleep,70 ; sleep for some time popad mov eax,ds:[7FFE02E4h] ; get new value of LastSystemRITEventTickCount sub eax,edx jz back ...
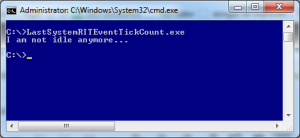
When ran, it waits for some user input (keyboard, mouse events) and only exits when these happen (sometimes more than one event is needed; this is probably caused by the update intervals).
Trivia fact: the very same value check is at the core of a function BeginIdleDetection.
An example demo program can be found here.