This is a little lolbin trick you can do with a nslookup.exe program.
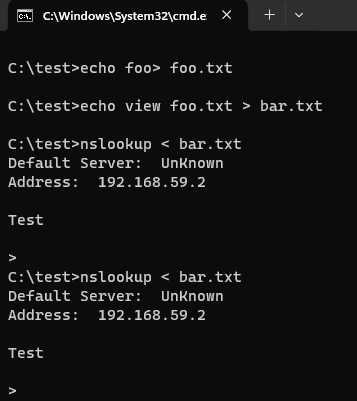
One of the less-known nslookup.exe commands is view <filename>. When executed, it reads a content of a given file and sorts it. The sorting bit is interesting to us as it is delivered by means of executing a command sort < %s | more.
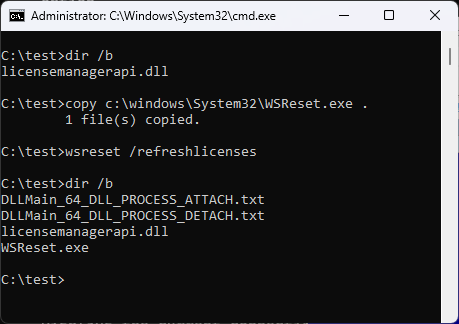
So, one can create a dummy file f.ex. foo.txt, then a nslookup-driving command file f.ex. bar.txt that includes a command to view the content of the foo.txt file, and then place a payload inside a sort.exe or more.exe program present in a local directory, and finally run nslookup with the input delivered from the bar.txt file – resulting in an execution of our payload: