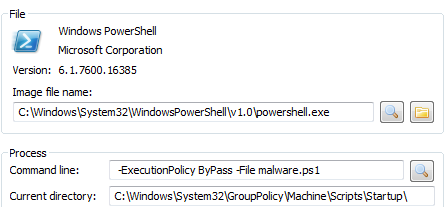
The need to test modules and the will to support legacy stuff have one thing in common – at least on Windows. These functions are heavily integrated with the system and both offer lots of various built-in mechanisms that can be used as an uncommon persistence mechanism. I have already described many of them, but recently I came across yet another legacy settings that we can add to our ‘dodgy autostart’ repertoire.
Let me introduce you to so-called Legacy CPL Mapping.
It is available since at least Windows 7, works under win10, and… it has to do with the way Control Panel Applets are launched; speaking pragmatically – there is a setting in Registry that helps to handle legacy Control Panel Applets.
The setting is stored in the following location:
- HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\
Control Panel\Legacy CPL Map
By opening a number of CPL files and filtering procmon logs to focus on the ‘Legacy CPL Map’ keys only we can quickly confirm that anytime the .cpl file is launched, the system ‘talks’ to the Registry to check the respective ‘Legacy CPL Map’ setting for the applet:
 The keys stored underneath include names of the Control Panel applets, and can be CPL names (f.ex. main.cpl), canonical names (f.ex.: Microsoft.PowerOptions, Microsoft.EaseOfAccessCenter), or DLLs (f.ex. ntvdmcpl.dll /this is the one that actually led me to this discovery/).
The keys stored underneath include names of the Control Panel applets, and can be CPL names (f.ex. main.cpl), canonical names (f.ex.: Microsoft.PowerOptions, Microsoft.EaseOfAccessCenter), or DLLs (f.ex. ntvdmcpl.dll /this is the one that actually led me to this discovery/).
Each key represent the legacy setting for a given applet and can contain one of two values:
- AppletCanonicalName
- ShellExecute
The first is a canonical name of the applet we wish to replace the legacy applet with (f.ex. could use ‘Microsoft.PowerOptions’). The name is then used by the IOpenControlPanel::Open method to launch the mapped applet.
The second is just a command line that will be passed to ShellExecuteEx function.
Obviously, both can be abused.
Let’s have a look at the easy one – the ShellExecute.
The settings:
- HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\
Control Panel\Legacy CPL Map\Microsoft.PowerOptions\ShellExecute
are being accessed when we click the ‘Additional Power Settings’ button under Settings\Power & Sleep:
By setting this value to calc.exe, we will launch the Calculator anytime someone tries to launch these settings:
This is what procmon sees when we click the button:
Of course, relying on Power Options is probably not enough – some users don’t touch it all. But… There is plenty of other .cpl files to look at…
- c:\WINDOWS\system32\appwiz.cpl
- c:\WINDOWS\system32\bthprops.cpl
- c:\WINDOWS\system32\desk.cpl
- c:\WINDOWS\system32\Firewall.cpl
- c:\WINDOWS\system32\FlashPlayerCPLApp.cpl
- c:\WINDOWS\system32\hdwwiz.cpl
- c:\WINDOWS\system32\inetcpl.cpl
- c:\WINDOWS\system32\intl.cpl
- c:\WINDOWS\system32\irprops.cpl
- c:\WINDOWS\system32\joy.cpl
- c:\WINDOWS\system32\main.cpl
- c:\WINDOWS\system32\mmsys.cpl
- c:\WINDOWS\system32\ncpa.cpl
- c:\WINDOWS\system32\powercfg.cpl
- c:\WINDOWS\system32\sysdm.cpl
- c:\WINDOWS\system32\TabletPC.cpl
- c:\WINDOWS\system32\telephon.cpl
- c:\WINDOWS\system32\timedate.cpl
- c:\WINDOWS\system32\wscui.cpl
Another interesting feature: one could add ‘c:\WINDOWS\system32\powercfg.cpl’, or any other .cpl to one of the standard Startup locations and it will never raise suspicion since it’s a Microsoft-signed binary. Once the Startup entry is launched, the calc.exe (or possible malware) will pop up!