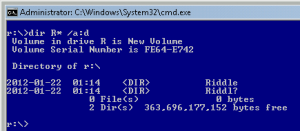
There are many answers here and the very same result could be achieved in many ways:
- Unicode/homomorph attack
using Unicode characters e.g. from Russian alphabet; this can be usually easily detected from a command line level:
- GUI attack
it is relatively easy to modify the content of any other window, including windows used by Explorer to display file names (window class is a standard ‘SysListView32′); some malware use GUI attacks to remove their processes’ names from a list of processes shown by Task Manager
- API hooking
trivial to return two exact file names for two different entries
- patching the file system entry directly
and probably a few more…