Things are never boring in the Visual Basic world. In part 20 I described how localization DLLs can be used as a potential persistence mechanism on the localized systems. Today, we will look at yet another localization feature offered by this platform.
Application in VB can be marked as localized by changing their internal language ID (LCID). They may also include a name for the localization DLL (two of them, actually).
In the example below, we can see a VB application marked as localized to German (the LCID is set to German=407h), the MSVBVM60.DLL will attempt to load the DLL marked szLangDll as well as szSecLangDll (as long as the latter is not equal to ‘*’ as in the below example).
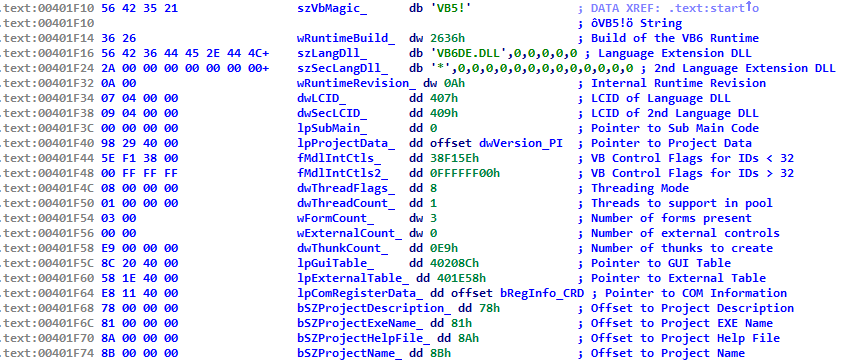 So, one way to ensure persistence is to find an existing VB app on the system, modify its internal LCID to a value different than the one on a local system and then place the respective localization DLL in the system directory as described in part 20. Another way would be modifying the embedded szLangDll name to something else and such dll would be loaded. Thirdly, we could modify szSecLangDll from ‘*’ to anything we want and such DLL would be also loaded.
So, one way to ensure persistence is to find an existing VB app on the system, modify its internal LCID to a value different than the one on a local system and then place the respective localization DLL in the system directory as described in part 20. Another way would be modifying the embedded szLangDll name to something else and such dll would be loaded. Thirdly, we could modify szSecLangDll from ‘*’ to anything we want and such DLL would be also loaded.
This is a pretty lame and is not far off from part 25 – a requirement to modify an executable is ridiculous for today’s standard, but I am adding it for completeness.
Bonus:
szSecLangDll is typically marked as ‘*’ – this is an internal marker that VB uses as an indicator telling the engine NOT to load the second localization DLL. Interestingly, I have seen Korean applications where this ‘*’ was changed to a tilde. I do not know why. If such application is found on the system this could be leveraged to develop a persistence mechanism based on such a tilde-based file name.
Have a look – we can see 3 persistence mechanisms at work here:

