It’s actually 99th, because I forgot one part on the way 🙂
This is one more persistence method based on a built-in set of features. This time the culprit is the Policy Manager.
Browsing through the PolicyManager key located here:
- HKLM\Software\Microsoft\PolicyManager\
we can spot many interesting entries, often multiple-level deep:

Some of them include entries that are of our interest:
- PreCheckDLLPath
- transportDllPath
The good news is that not all entries have them a.k.a. they are optional. And it turns out that these allows to provide additional utility libraries that in turn will be loaded by Policy Manager components (policymanager.dll) when this DLL itself is utilized.
I couldn’t come up with a quick& dirty way to load the test dll, so I cheated by starting the procmon, setting up the filters, and letting it go for some time. After awhile I caught the first process accessing these entries:
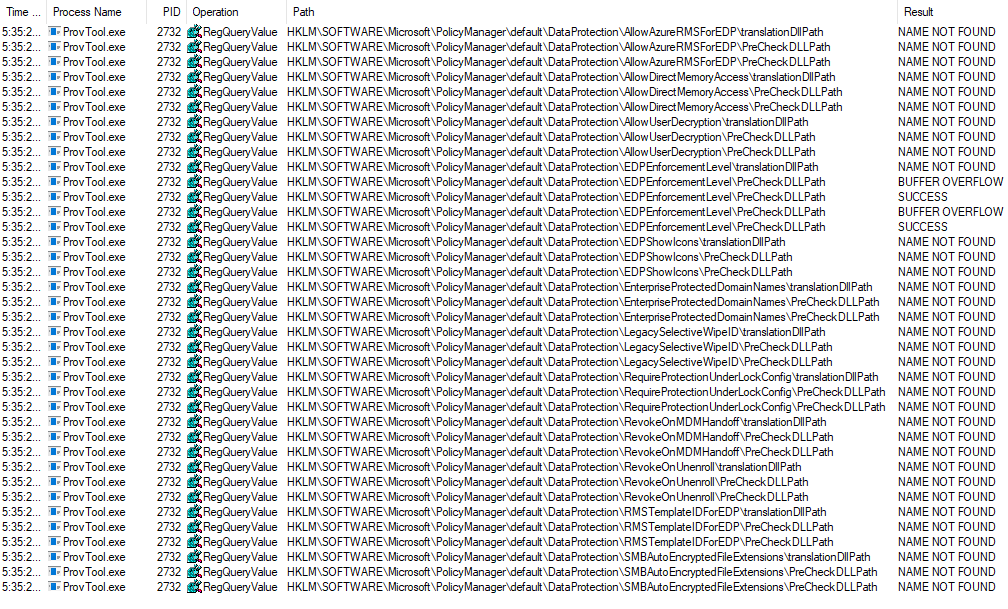
The harvesting may be easier on a system connected to the domain (policies deployment/access is more frequent).

