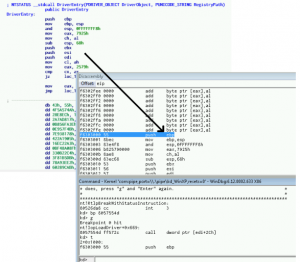
One of pieces used by Purple Haze malware is its driver (c:\WINDOWS\Temp\2.tmp) loaded by NtLoadDriver API. It can’t be directly loaded into IDA for analysis, because it contains a layer of protection. One way to bypass it is to use some good anti-rootkit tool e.g. xuetr and dump the malicious kernel driver from memory after it is loaded and decrypted. Since this may not work all the time, sometimes it’s better to control the execution flow through windbg right from the DriverEntry via a well-known IopLoadDriver+xxx trick. Using windbg has many advantages as we can dump physical memory anytime we wish or poke around the code and map findings to IDA as we go along, we can also see decryption in action and prevent any actions driver may take to wipe out the content of memory or detect debuggers.
In this particular case xuetr worked, and dumping the driver directly from memory is a piece of cake – after fixing the section alignments we can finally load it into IDA.
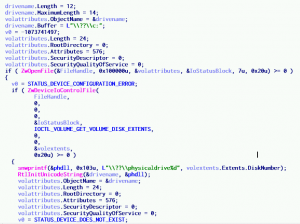
btw. if you use IDA’s built-in VOLUME_DISK_EXTENTS structure, you need to fix it as it doesn’t take into account an 8-byte alignment of data – structure members are placed at incorrect offsets (this is not obvious and original MS headers also don’t mention it explicite, so it can be a bit misleading).
00000000 VOLUME_DISK_EXTENTS struc ; (sizeof=0x18, standard type) 00000000 NumberOfDiskExtents dd ? 00000004 Extents DISK_EXTENT ? 00000018 VOLUME_DISK_EXTENTS ends
correct:
00000000 VOLUME_DISK_EXTENTS2 struc ; (sizeof=0x1C) 00000000 NumberOfDiskExtents dd ? 00000004 padding dd ? 00000008 Extents DISK_EXTENT ? 0000001C VOLUME_DISK_EXTENTS2 ends
similarly
00000000 DEVOBJ_EXTENSION struc ; (sizeof=0x8, standard type) 00000000 Type dw ? 00000002 Size dw ? 00000004 DeviceObject dd ? ; offset 00000008 DEVOBJ_EXTENSION ends
is more useful with extra fields:
00000000 DEVOBJ_EXTENSION2 struc ; (sizeof=0x29) 00000000 Type dw ? 00000002 Size dw ? 00000004 DeviceObject dd ? 00000008 PowerFlags dd ? 0000000C Dope dd ? 00000010 ExtensionFlags dd ? 00000014 DeviceNode dd ? 00000018 AttachedTo db ? 00000019 StartIoCount dd ? 0000001D StartIoKey dd ? 00000021 StartIoFlags dd ? 00000025 Vpb dd ? 00000029 DEVOBJ_EXTENSION2 ends